



Single sign-on (SSO) is an authentication method used by companies to centrally manage employee access. Using an SSO identity provider, IT admins can control in one place who can access any services used by the company. This is ideal for IT admins when onboarding new employees, as it provides them with instant access to multiple software services (avoiding the need to register new employees to these systems one by one). Offboarding employees is also simplified, as access from all systems can be revoked in one place. Employees also benefit as they can access all the programs they need by using just one set of credentials.
All your team members will be able to sign in to KAYAK for Business with their IDP account (e.g. Google, OKTA etc.) If you choose to require SSO, your members will see a sign in page before they can access your workspace. The admin(s) for your KAYAK for Business account don’t have to add new users manually to your KAYAK for Business account.
You can get more information on Azure SSO Integration and user provisioning on this tutorial page.
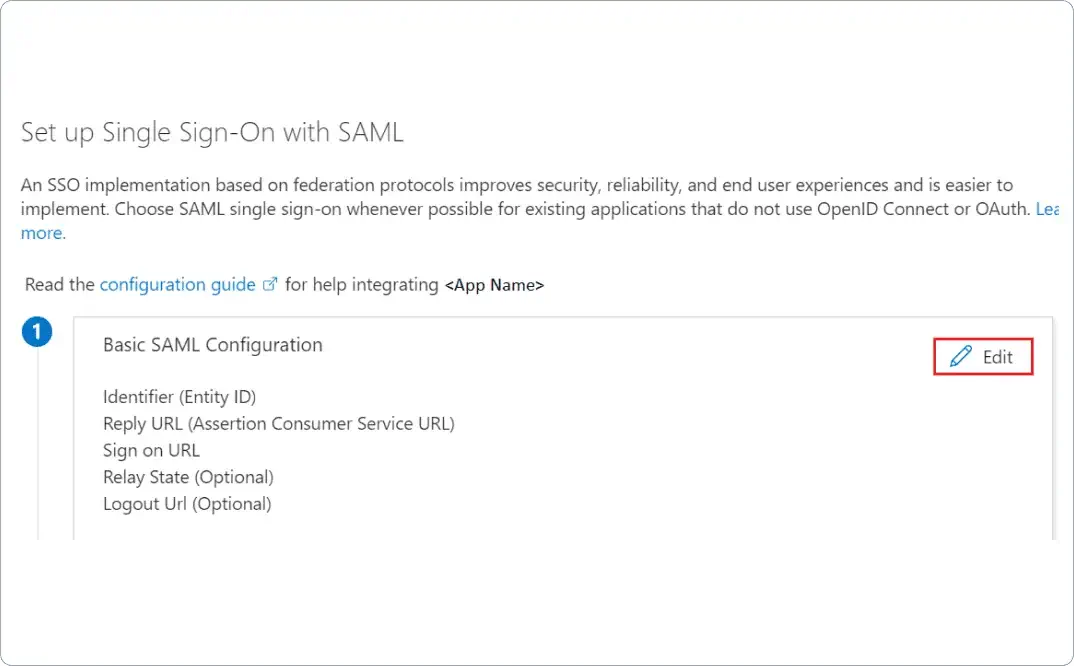
Here you can find further information on setting up a SAML based SSO from Okta.
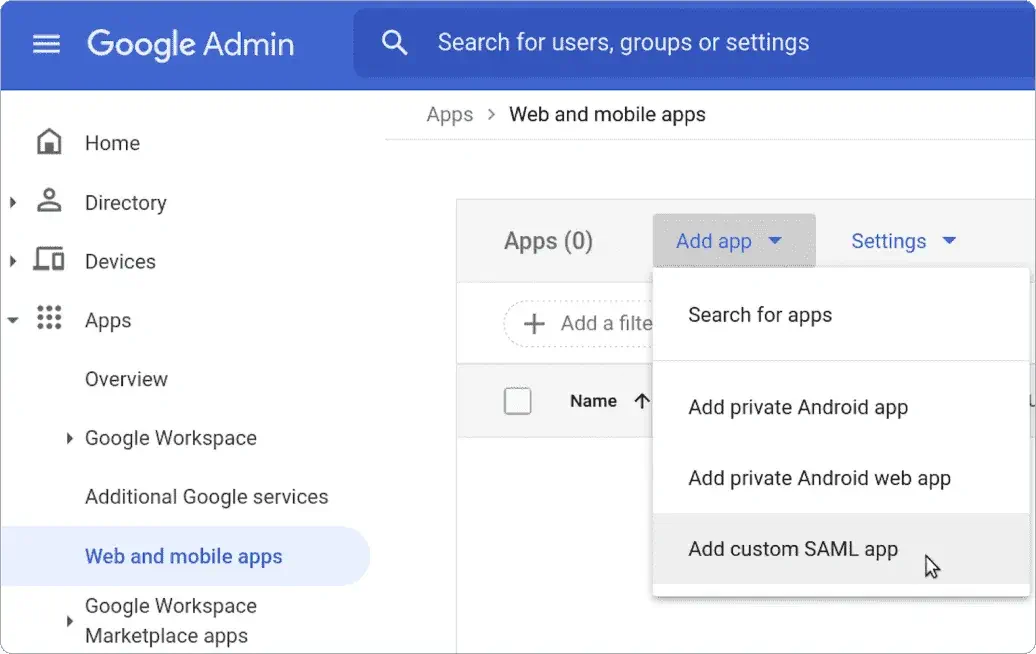
Here are some best practices for connecting your Google SSO with an IdP SAML Apps Configuration.
You can update your SSO setup any time (just need to make sure they do not lock themselves out). Also, you would need to make sure that their external user IDs remain the same between the systems. i.e. if you use emails as ID on your existing IdP, then the same emails must be used on the new system as IDs. Otherwise we would not be able to match the user who is logging-in to their existing account.
Your IdP identifies that the user profile is no longer in your company’s system, therefore the attribute mapping to your KAYAK for Business account for that user will no longer work at the attempt of signing in. You can remove the user from your KAYAK for Business company account from the Manager Users section.
In this case, you can simply go to your Manager SSO section and update your token in the space where the existing token is living.
In this case, it is recommended to double check if your IT team has granted access to all user groups for them to login from their IdP (e.g. Google SSO, OKTA etc.) to the third party application.
Here you can find the lift of common issues related to Google’s SSO configurations. You can find tips and advice for troubleshooting your issue according to the response or error message you receive.
Your workspace owners and/or organisation Identity Provider (IdP) owners from your company are able to activate this feature. Usually, the IT department from an organisation will know how to activate this, therefore please reach out to your IT team if you’re unsure how to get this integrated.
They can login with their work email directly to KAYAK for Business, since your company’s SSO is connected to your KAYAK for Business account.
KAYAK for Business supports all Identity Providers, including OKTA, Microsoft Azure AD, G Suite and OneLogin. KAYAK for Business currently only supports SAML Integration, and OAuth integration is a work in progress.
Your SSO administrator needs to map the user’s attributes on the KAYAK for Business SSO Integration page according to the user attributes given in your Identity Provider. The attributes are the first name, surname and email of the user. If there is any discrepancy between the attributes given on KAYAK for Business and your Identity Provider, the integration can not be completed.
Currently, KAYAK for Business only supports SAML SSO Integration. OAuth Integration is a work in progress.
California consumers have the right to opt out of the sale* of their personal information. For more information on how we securely process personal information, please see our Privacy Policy.
Do not sell my info
* The definition of "sale" under the California Consumer Privacy Act is applicable only to California consumers.